Reading Time: 4 minutes When it comes to safeguarding an organization’s assets, insider threats are among the hardest to detect. Malicious internal users often have legitimate access to systems, making their actions harder to identify until damage is done. This is where audit log alerts can play a crucial role. By leveraging real-time notifications and anomaly detection, organizations can uncover suspicious behavior and respond before it escalates into a serious breach.
Internal threats stem from individuals within the organization, including current or former employees, contractors, or business associates. Internal threats can be particularly damaging due to the insider’s knowledge and access to sensitive systems and data. Notably, malicious insiders accounted for 12% of breaches in 2022, with an average cost of $4.18 million per incident, per IBM and Ponemon’s 2024 “Cost of a Data Breach” report.
Panzura Data Services is an extension to the Panzura CloudFS hybrid cloud file services platform , providing a single, unified view and management of unstructured data within CloudFS. Data Services ingests both metadata and audit log data from CloudFS when enabled, to enable visibility and observability over the global file system and related infrastructure, and offer lightning fast file search, audit, recovery and analysis across files in CloudFS.
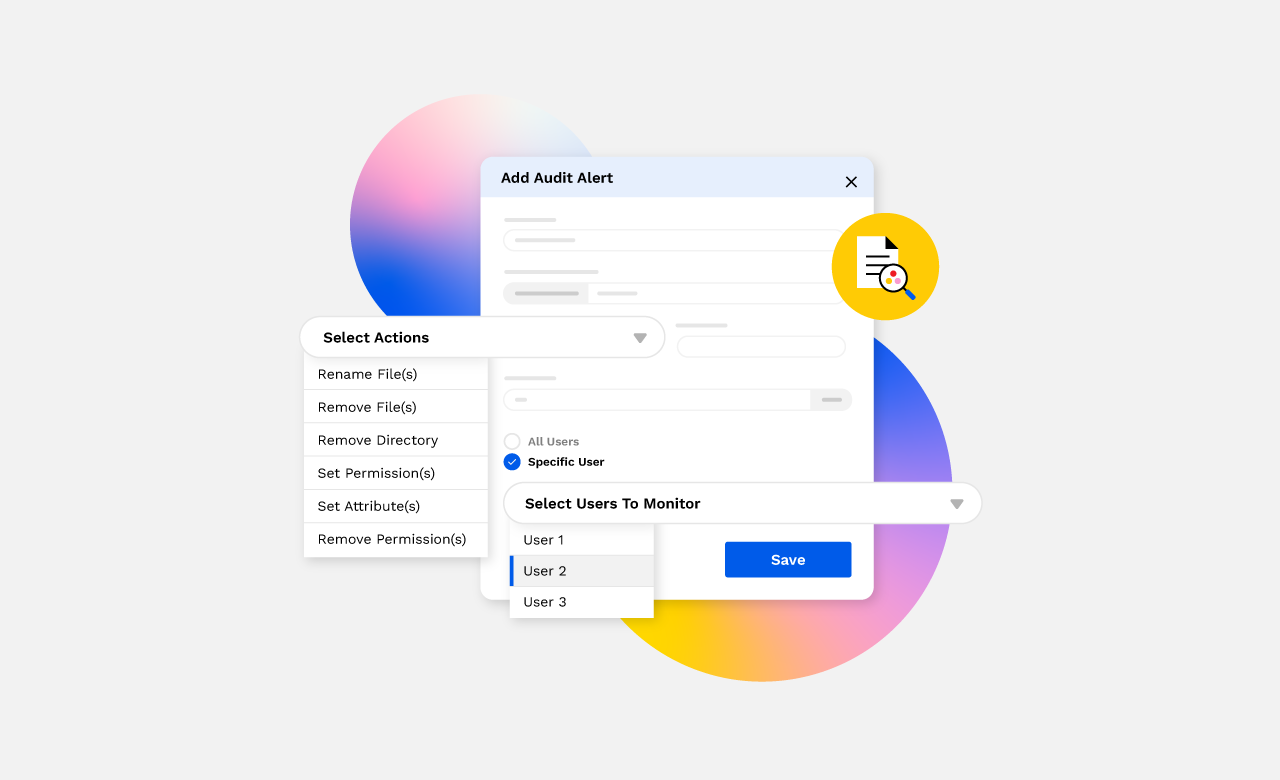
New in Data Services: Audit Policies and Audit Log Alerts
Audit log alerts can play a crucial role in enhancing security and operational oversight by monitoring various activities:
Tracking Data Exfiltration : By setting up alerts for unusual data transfers, you can detect when sensitive information is being moved out of your network, potentially indicating a data breach.Identifying Information Destruction : If critical files are deleted or altered, audit log alerts can immediately inform you, allowing for quick action to recover data and investigate the cause.Spotting Anomalous Activity : By monitoring for unusual patterns of behavior, such as accessing or copying multiple files in a drive containing sensitive information, audit log alerts can help identify potential security threats or insider threats.
These capabilities enable organizations to maintain a high level of security, ensure compliance with regulations, and respond swiftly to potential incidents
Setting Up Effective Alerts To use audit log alerts effectively, you need to start by identifying behaviors that could indicate malicious intent and building policies around them. This includes actions like accessing restricted files or attempting to escalate permissions without authorization.
For example, if an employee copies or moves a large volume of sensitive files within a short period—especially outside of normal working hours—this could signal data exfiltration. By configuring an alert to monitor such activity, you can flag the behavior for immediate review.
Panzura Data Services allows you to set up behavior-based or threshold-based alerts based on audit policies. Behavior-based alerts focus on deviations from normal patterns, while threshold-based alerts trigger notifications when certain activity exceeds predefined limits. Combining these approaches provides a robust safety net against insider threats.
Automating Responses for Speed and Efficiency One of the key benefits of audit log alerts is their ability to trigger automated responses. For instance, if an alert identifies a potential privilege escalation attempt, Data Services' alerting to the security team can trigger a script to automatically roll back the changes. Similarly, in cases of unusual login attempts, the account can be temporarily locked until further verification.
These automated actions minimize potential damage, giving security teams time to investigate the incident without compromising critical systems.
Centralizing and Refining Alerts Managing alerts across multiple systems can quickly become overwhelming, and introducing additional alerts from Data Services might seem like it could add to the noise. That’s why Panzura Data Services seamlessly integrates with SIEMs like Rapid7, providing centralized, streamlined alert management for improved efficiency and clarity.
However, no alert system is perfect from the start. Regularly reviewing and refining alert configurations is essential to reduce false positives and ensure new threats are accounted for. For example, adjusting thresholds or incorporating feedback from past incidents can significantly improve the accuracy of your alerts.
Audit alerts are now available to Panzura customers with Panzura Data Services audit tier. For complete information on Panzura Data Services, take a look at the technical whitepaper .
Alerting On The Other 88% of Threats Panzura’s Detect and Rescue works hand-in-glove with Panzura Data Services to parse and assess file operations within CloudFS in near real time, looking for anomalies, such as ransomware, malware and other threats. It can also take action, if suspicious activity is detected across multiple files in a short period, the system will interdict it by automatically shutting off write access for the affected user or users. This prevents further damage or data modification while the security team investigates the issue.
Panzura Detect and Rescue extends and bolsters the data resilience capabilities of the CloudFS hybrid cloud file platform by providing active storage protection to minimize disruption and maximize business continuity.
For more information on Detect and Rescue, check out the product brief.