| Traditional Security | CloudFS | |
|---|---|---|
| Detection Method | ||
| Threat Scope | ||
| Admin Effort | ||
| Response | ||
| Coverage | ||
| Data Integrity | ||
| Operational Impact | ||
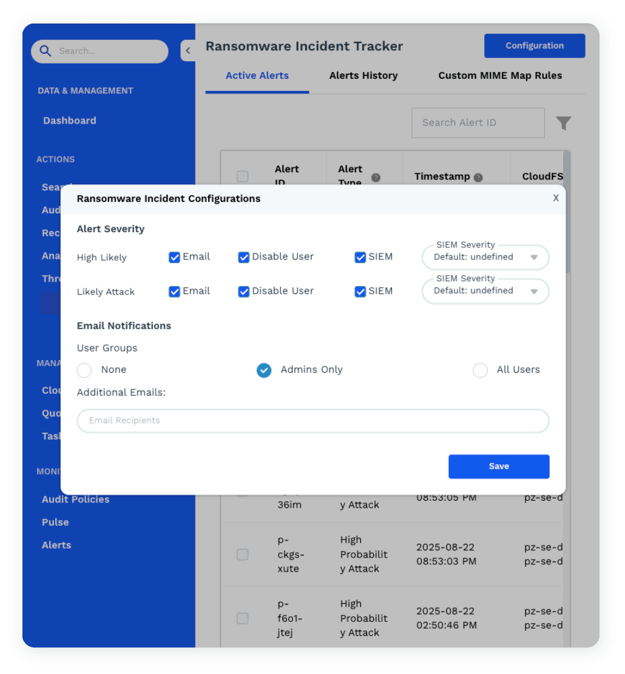
THREAT CONTROL FOR PANZURA CLOUDFS®
Protect Your CloudFS File Data from Attack with AI
Threat Control For Panzura CloudFS is an AI-powered security layer integrated into the Panzura global file system that uses machine learning to proactively identify ransomware, data exfiltration, and mass deletions. The system monitors files in real-time to detect subtle behavioral anomalies without impacting the performance of active user workloads. By combining this predictive intelligence with an immutable data architecture, it can automatically disable compromised accounts and enable fast recovery for business continuity.

Intelligent Security for Hybrid Cloud File Data
Threat Control capabilities of CloudFS provide a proactive solution to the challenges of hybrid cloud file security. Traditional security methods are often reactive, relying on signature-based tools that lead to alert fatigue and leave you vulnerable to new threats. With CloudFS, you can transform your file infrastructure into a powerful security layer.
Key capabilities include:
-
Proactive Threat Detection: Instead of relying on a database of known threats, CloudFS uses advanced machine learning to create a unique behavioral fingerprint for each user.
-
Early Warning System: The system detects subtle deviations from normal user activity, providing early warning signs of a potential attack.
-
Automated Threat Response: CloudFS takes immediate, proactive action to stop threats, preventing data loss, exfiltration, and ransomware from causing harm.
-
Reduced Manual Remediation: By stopping threats early, CloudFS reduces the need for time-consuming and resource-intensive manual remediation after a breach.
This intelligent approach gives you the control and insights needed to stay ahead of the threats and protect your critical data.
The Proactive Detection Advantage
At the heart of the Threat Control capabilities lies advanced ML techniques, meticulously building intelligent behavioral profiles for every user and every file interaction based on your own CloudFS environment. This isn’t basic anomaly detection. CloudFS continuously analyzes vast datasets – potentially millions of data points daily – to establish a precise baseline of normal activity. This intelligence allows CloudFS to accurately identify even the most subtle deviations, giving you the confidence that your hybrid cloud file data is protected by a system that truly understands and anticipates threats, rather than focusing only on disaster recovery.
-
Reduced Manual Effort: Automated detection and response, freeing up valuable admin time.
-
Identify Threats: Behavioral profiling identifies unknown and emerging threats.
-
Ensuring Data Integrity: Proactive protection against corruption and exfiltration.
-
Regulatory Compliance: Comprehensive, auditable data security for regulatory requirements.
Traditional File Security vs. CloudFS Threat Control
CloudFS “Defense in Depth” Approach
Building on CloudFS’s industry-leading data protection, resilience, and recovery capabilities, the enhanced Threat Control feature set delivers what security experts call “defense in depth.”
This layered approach to data management ensures attackers must defeat multiple different protection mechanisms to cause lasting damage.
The platform’s immutable architecture guarantees that even if a threat bypasses detection, attackers cannot destroy recovery points, which eliminates slow backup dependency and dramatically cuts investigation time and financial losses.
Layered approach ensures attackers must defeat multiple different protection mechanisms to cause lasting damage.
Data Exfiltration
Detects when large volumes of data are being accessed or copied in patterns that are unusual for a specific user.
Data Destruction
Recognizes suspicious damaging behavior, like mass deletions, that signal an active ransomware attack.
Unusual Behavior
Flags erratic access patterns, bulk file creation, or after-hours activity that doesn’t match established user profiles.
Ransomware
Catches known and unknown ransomware based on signatures, encryption, and suspicious file behavior.
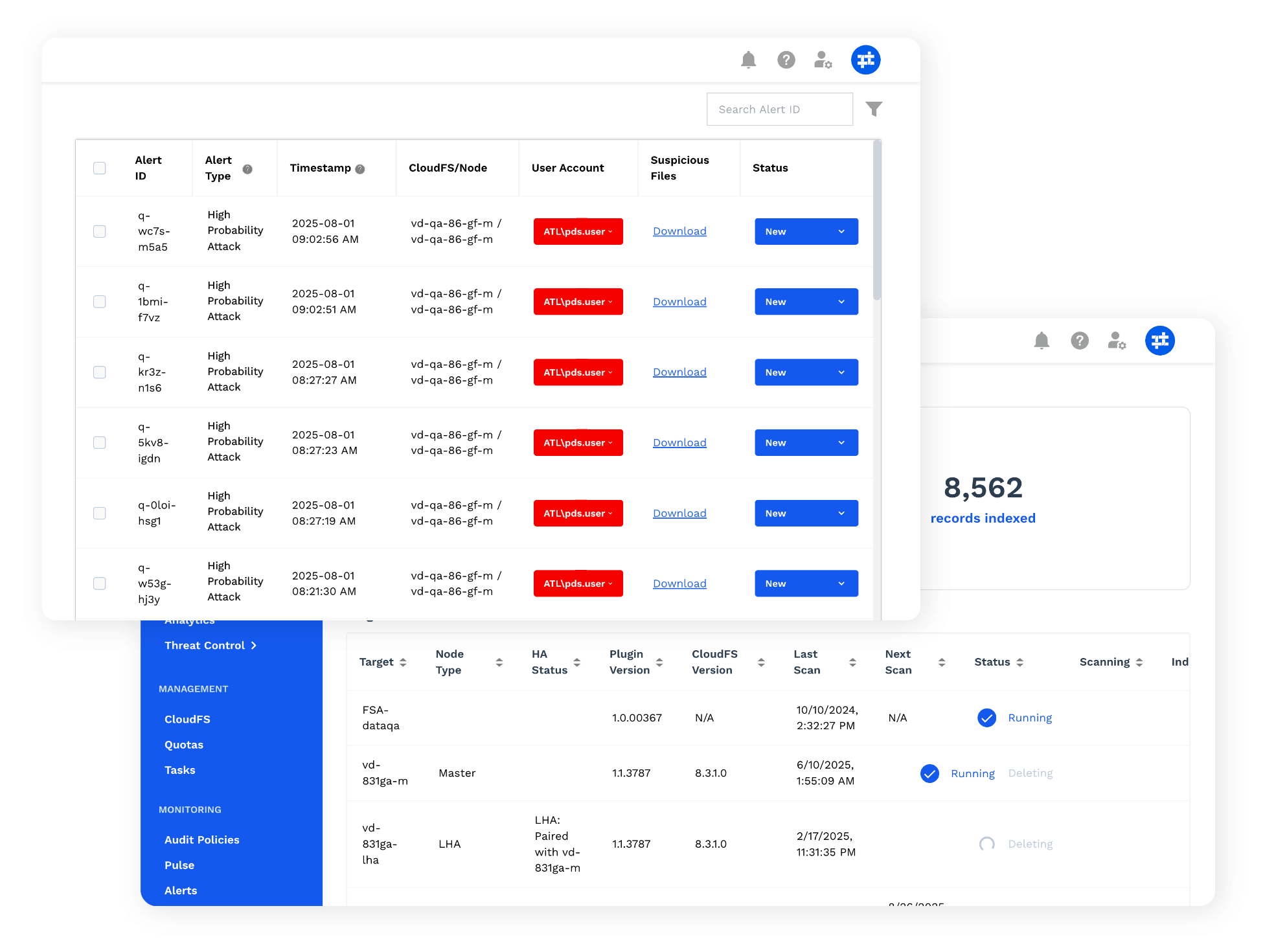
Secure Your Files without Compromising Performance
Curious how CloudFS Threat Control delivers proactive defense? It’s a smart, seamless process. Advanced ML continuously ingests your file activity, building intelligent behavioral profiles for every user. When any activity deviates from these learned patterns – the early signs of a threat – the system instantly detects the anomaly and triggers a proactive response. This intelligent flow is easily accessed in your CloudFS dashboard, and gives you a clear look “under the hood” so you can have confidence in the security of your CloudFS environment.
The core of this innovation lies is a unique two-tiered architecture:
- A cloud-based system efficiently monitors file activity by analyzing metadata to spot anomalies. This offloads resource-intensive scanning and avoids the constant background burden that slows down user devices. This analyzer is fed new and changed metadata in near real-time, allowing for rapid identification of and reaction to behavioral changes.
- A lightweight agent remains dormant until the system flags a potential threat. It then activates for a targeted, deep scan of the actual file content. This ensures sensitive data never leaves the local environment, preserving both privacy and performance. This approach avoids constant, heavy-duty scanning that slows down users.
Move Faster Than Threats
Stop an attack in its tracks before it cascades across your network. CloudFS detects threats at the earliest possible stage – the file system itself.
Zero-Touch Approach
Reduce alert fatigue with a “zero-touch” approach that creates user profiles and adapts to legitimate baseline changes automatically.
Seamless Implementation
Threat Control is seamless for CloudFS customers. There are no infrastructure changes, no user disruption, and no complex configurations needed.
Automated Tiered Response
CloudFS logs anomalies, notifies admins, and even disables compromised accounts – eliminating the human errors and delays that can cost millions.
Eliminate Data Loss and Downtime with Consolidated DR/BC and the Industry's Fastest RPO
CloudFS leverages its immutable architecture and snapshot technology for powerful recovery in the event of accidental data loss or a cyber incident. The system maintains a single, authoritative dataset in the cloud object storage, eliminating the need for traditional data replication across multiple on-premises NAS devices for backups and disaster recovery.
The platform creates immutable snapshots every 60 seconds, which cannot be altered or encrypted, making them resistant to ransomware and other data corruption. You can instantly restore your entire file system or even a single file with a near-zero recovery point objective (RPO) – the fastest in the industry according to Frost & Sullivan – and a recovery time objective (RTO) of mere minutes. This approach consolidates DR/BC and delivers high availability with data resilience.
The Real Impact of AI-Powered Cyberstorage
The following summarizes the industry-benchmarked impact of AI and ML on cybersecurity performance metrics, providing a clear foundation for the quantifiable benefits of AI-powered Threat Control in CloudFS.
| Performance Metric | Industry Average Improvement | |
|---|---|---|
| Section Title | ||
| Describe Feature Here | False Positive Reduction |
[1] Up to 90% (from behavioral analysis & ML) |
| Describe Feature Here | Incident Response Time Reduction |
[2] 96% |
| Describe Feature Here This is a great place to add a bit of extra information about the feature. |
Zero-Day Threat Detection Improvement |
[3] 70% |
| Describe Feature Here | Phishing Success Rate Reduction |
[4] 86% |
| Describe Feature Here | Cyberattack Success Rate Reduction (Behavioral Analysis) |
[5] 73% |
| Describe Feature Here | Data Breach Prediction |
[6] 85% |
APT Detection Speed |
[7] 5x Faster |
|
Additional CloudFS Threat Control Resources
-
Get a Personalized Demo
-
Download the Product Brief
-
Read the Blog: “CloudFS Just Got Smarter with AI-Powered Threat Control”
-
Read the Blog: “A Deeper Look at the Performance and Privacy Advantage of CloudFS Threat Control”
-
See the Press Release: "Panzura CloudFS Reimagines File Data Defense with New AI-Powered Threat Control"
Threat Control FAQs
-
How do modern file data systems move beyond traditional, reactive security models to proactively stop ransomware and data exfiltration?
Modern file systems like Panzura CloudFS shift to a predictive security model by using AI-powered behavioral analytics. This enables them to learn normal user activity and proactively identify and neutralize threats like ransomware and data exfiltration in real time, often before they escalate into business disruptions.
-
What is behavioral fingerprinting, and how does it help a file data platform detect unknown threats?
Behavioral fingerprinting is a method where an AI-powered file system creates a unique profile of a user's typical file activities. The Threat Control engine in Panzura CloudFS uses this baseline to instantly detect subtle, but potentially problematic, deviations that may signal a new or unknown threat without relying on traditional signatures.
-
How can a file system address "alert fatigue" for IT teams while still providing reliable data protection?
The Panzura CloudFS Threat Control feature addresses alert fatigue by providing a "zero-touch" approach that focuses on detecting specific anomalies, such as mass deletions or data exfiltration. This proactive, behavioral-based approach significantly reduces false positives and automates responses, minimizing the need for constant manual intervention.
-
How does can a file data platform's security architecture protect file data without compromising performance?
Panzura CloudFS has a patent-pending two-tiered security architecture that centralizes initial monitoring to offload the computational burden. A lightweight agent performs detailed inspection only when a potential threat is flagged, ensuring data confidentiality and maintaining performance without resource-intensive client-side scanning.
-
What is the role of immutable data and snapshots in a "defense in depth" cybersecurity strategy for file data management?
Immutability and snapshots serve as a final, critical layer of defense in the Panzura CloudFS file system. This architecture ensures that even if a threat bypasses initial detection, attackers cannot destroy recovery points, which guarantees data is secure and enables a rapid recovery.
-
How can a file data system use AI to automate threat response and prevent an incident from becoming a major business disruption?
Panzura CloudFS uses advanced ML to automate responses to high-severity threats, such as instantly logging anomalies, notifying administrators, and disabling compromised accounts. The platform's tiered automated response framework eliminates the human delay that can cost millions, preventing an incident from escalating.
-
How can an enterprise-grade file system help an organization reduce its total cost of ownership (TCO) while enhancing security?
Panzura CloudFS helps reduce TCO by consolidating disparate file management and security functions into a single platform, eliminating data and infrastructure sprawl. Its global file system architecture with granular deduplication and compression significantly reduces the data footprint, leading to lower cloud storage and licensing fees.

Ready to take a look?
Stop struggling with uncontrolled unstructured data growth and sprawl. Open up visibility, resilience, and immediacy with intelligent hybrid cloud solutions that put you back in control.



